
Imagine a laptop without an operating system. Do we need that kind of a laptop? What do we do with such a laptop? And how can we use it?
These days, laptops have become an essential part of people’s life. In that case, above-mentioned situation will be a nightmare as we all know that a laptop must run on top of an OS. I think we should explore more about these OSs.
Well, when we move forward with the OSs, there are some important functions of an operating system. According to some resources, the first and key function is “security”. A technology-based work without security is like a house-door without a lock. Unfortunately, now we can see security is the main issue in the technical world. While exploring OSs with good security, we can find one strange OS. That is the “QUBES OS”.
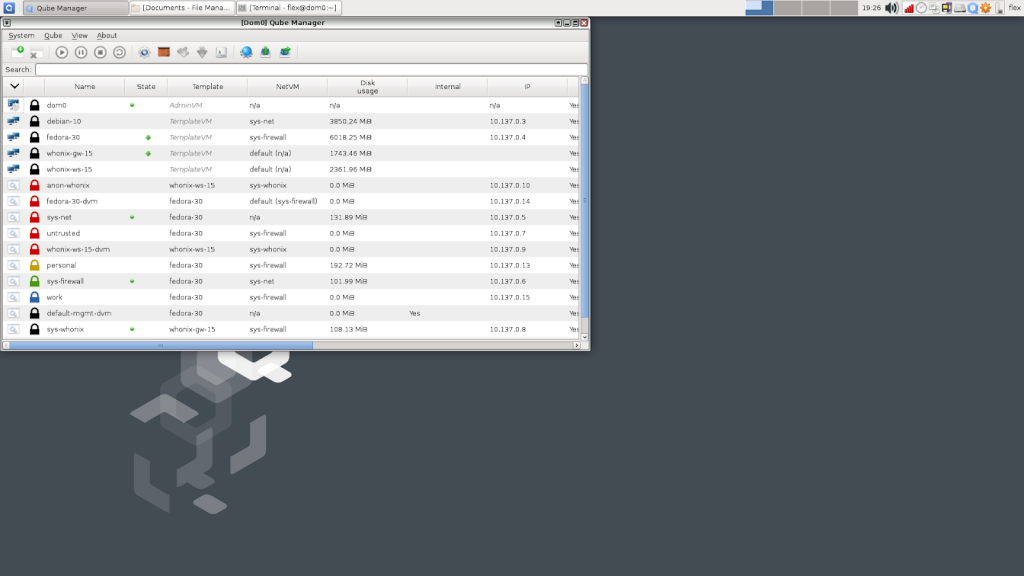
Qubes OS is the most secure OS in the world from the OS distributions. It’s mainly based on fedora but we can change that base as well. Qubes implies cubes, which acts as boxes inside a box. This is not an ordinary OS, which is not only for log and work. We have a control panel in this OS and there are cubes that we have created. Personally, we can have some templates by default. Mainly, there is a Dom-0 as Qubes OS and also we can have templates as Debian OS, Fedora and Whonix. As we can find there are three main secure OSs. That is QUBES OS, Tails OS and Whonix. Between those three OSs, Tails and Whonix OSs are going through as the tor based OSs but the Qubes OS is going through the completely different path.
As mentioned above there are cubes similar to VMs. The main cube is Dom-0 and it has the Qubes OS. There is a Sys-net as the first cube. It’s regarding the network. So the internet comes to Sysnet directly. Also, there is a Sys-firewall as the second cube which is the firewall. All of these cubes are created on various templates.
Dom-0 – Basically, this is based on Fedora but if want, we can change it. Now it’s on Fedora 30.
Sys-net – This is based on the Fedora template/OS
Sys-firewall – This is based on the Fedora template.
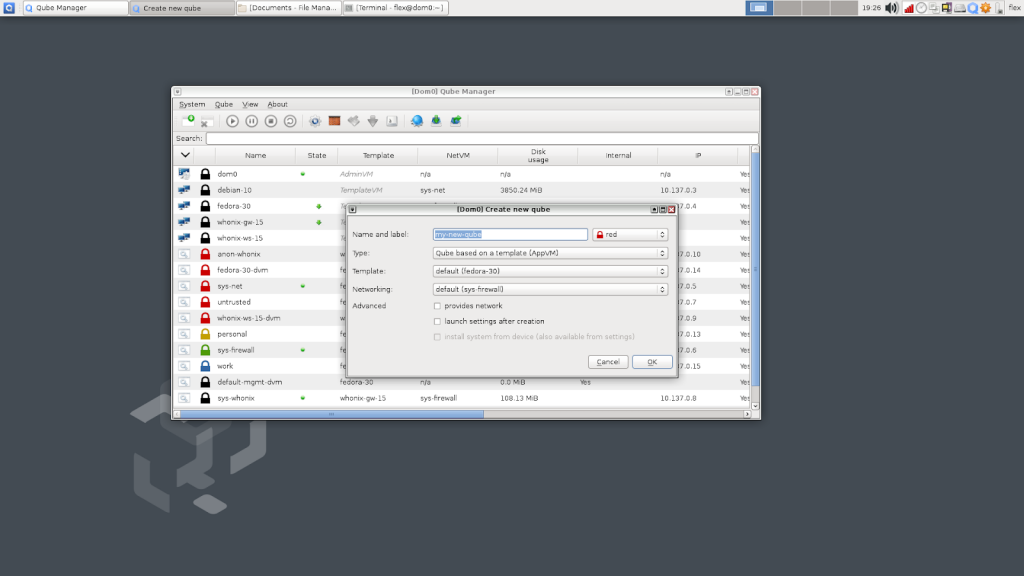
Besides, they may have created some cubes by default like personal and work and also, we can create more new cubes. This OS allows to delete the cubes we created as well. When creating new cubes we have to give the base by selecting one from Fedora, Debian or Whonix. And also needs to give the network by selecting one from Sys-net or Sys-firewall. Likewise, we can choose a set like that.
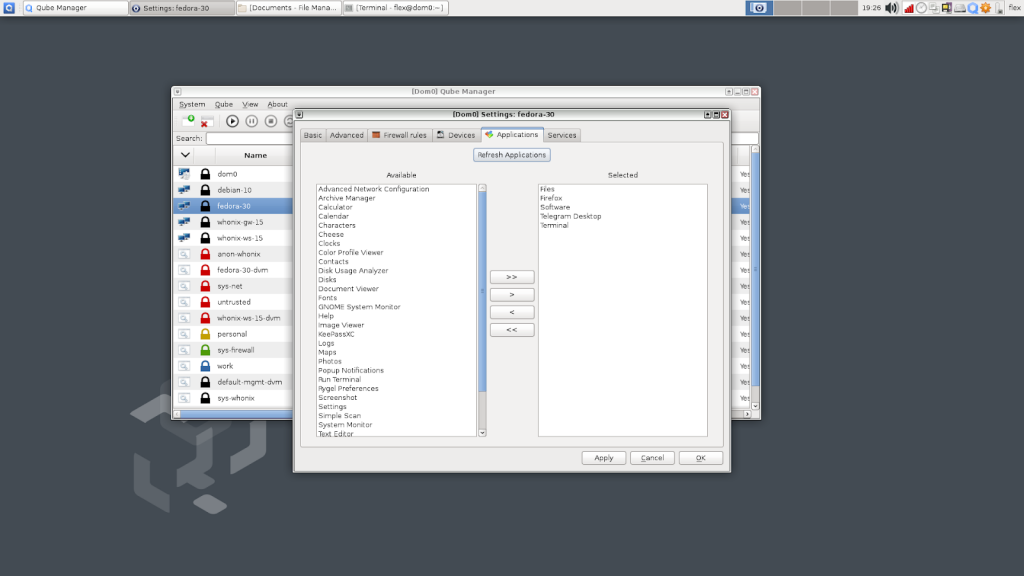
The start menu has all cubes/templates that are currently available. These cubes are in a shutdown mode. In there we have the applications that we have allowed. So if we click an application, then that cube is starting on. After starting on that VM, that application opens in that applicable cube. We can see that the above operation on the control panel.

How to install an application
There are some methods to install applications.
- We can install with the base template and allow the other cubes
- Or We can install applications cube wise separately.
Fedora store has given to fedora templates directly. If we want to install an application to a VM, the normal installation method is not the correct method here. Let’s assume that a user has 2 accounts in the same application, So as the first method he doesn’t want to install that application in two cubes for those 2 accounts. The user can simply install that application through the fedora software centre because of those cubes based on fedora OS. After installing, the user can go to those cubes and there are applications that can be allowed. So the user can allow those applications as his preferences. After doing that, those allowed application continuously available. Moving forward with the second method, we can install application cube wise separately.
Finally, after a ride around the QUBES OS, I thought that ride is really interesting and curious. Hope using a Qubes OS is going to be a new and safe experience for everyone.

